The Astor IV Technique Generator (TG)
Electronic Attack (EA) & Electronic Support (ES)
System attributes:
| Frequency coverage (one TG per band): | S-band (E/F), C-band (G), X-band (H/I/J) and Ku-band (J) |
| Output power | >+10 dBm |
| Sensitivity: | Typically better than -65 dBm |
| Minimum delay: | <100 ns |
| Prime power: | 28 VDC |
| Power consumption: | <170 W |
| RF connector | SMA |
System capabilities:
The Astor IV TG contains a receiver and three parallel jamming channels: two wideband DRFMs and one wideband SOR. This creates the ability to combine obscuration jamming and deception jamming. The techniques, that are fully user programmable, are:
- Barrage noise
- Spot noise
- Spot noise with frequency memory
- Pulsed noise
- RGPO/I, VGPO/I
- Cover pulse with or without accelerating edges
- False targets
- DRFM CW
- Multiple false targets
- Pattern projection (project a picture in the radar)
- TETRIS (special high density false target technique)
- Asynchronous pulse train
In addition, amplitude modulation (AM) can be applied to any technique and phase/frequency modulation can be applied to any DRFM technique.
The AM techniques are:
- Constant gain
- Constant gain with delay
- Inverse gain
- Square wave/swept square wave
- Sawtooth/swept sawtooth
- Sine/random sine
- Count down
The phase/frequency modulations are:
- Frequency sweep
- Random frequency modulation
- Coordinated doppler (coordinated with false target range motion)
- Phase noise and binary phase noise
- Binary phase shift keying
- XRN (special alternating sideband modulation)
- Chirp
Jamming techniques can be scheduled in time to create jamming sequences.
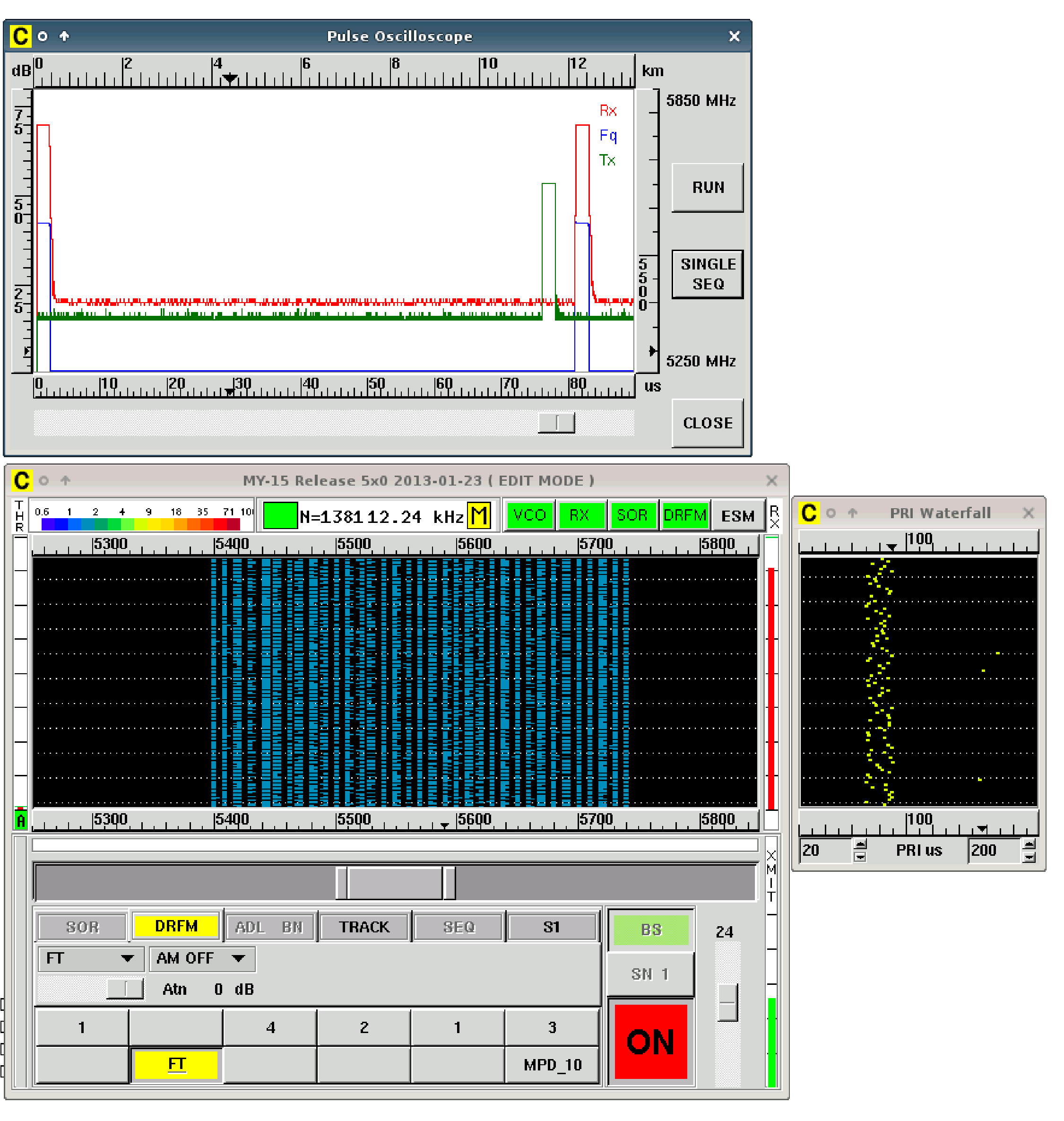
The System contains a PRI tracker that can identify fix, dwell & switch, stagger, sliding and jitter PRI. The primary purpose of the tracker is to support the generation of up-range false targets even if the radar uses agile PRI.
All user data (jamming techniques and log files) are stored on a USB key and the system contains no user data after power down.
The System can also perform threat emitter simulation (TES) with a pre-programmed arbitrary waveform.
The evolution from Astor III to Astor IV has resulted primarily in enhanced DRFM capabilities (dual DRFMs, greater memory depth, 40 us vs. 437 us, and wider bandwidth, 750 MHz vs. 2,3 GHz, in Astor IV) and added jamming techniques (count down and chirp).
HMI:
The HMI has an extensive mode editor with animations of the programmed technique. The receiver data is presented in a waterfall display. In addition there is an oscilloscope showing detector signal, frequency signal and transmitted signal, and a PRI waterfall.